Supported databases
Via connections and the operators
- Read Database
- Write Database
- Update Database
- Execute SQL
Altair AI Cloud supports relational database systems offering a fully compliant JDBC driver.
Whitelists
For the following databases, a subset of drivers are whitelisted:
Altair Graph Studio & Lakehouse
| driver | checksum |
|---|
| altair-graph-21.0.8171.jar | df8bfc6bb59f4fe6c09fe9f98c0794e3 |
Apache Cassandra
| driver | checksum |
|---|
| cassandra-driver-extras-3.11.5.jar | 7ba1b270f9e62403e751f9e138bc0a5e |
Apache Hive
| driver | checksum |
|---|
| hive-jdbc.jar | 6920f1b68b9c0eabf0e7a2a45f74006d |
Databricks
| driver | checksum |
|---|
| DatabricksJDBC42.jar | 918a96cf1809f5788caa1e150e8d5c27 |
| DatabricksJDBC42.jar | c2adb7d313fa26073785e9dee901b09b |
Google BigQuery
Google BigQuery's JDBC driver performance is limited. We recommend using the Google Cloud connector instead, which supports OAuth 2.0 authentication with User Account, Service Account, or Workload Identity Federation protocols.
| driver | checksum |
|---|
| GoogleBigQueryJDBC42.jar | 6ece0c00f0b4395b65b2772ec2951196 |
HSQLDB
| driver | checksum |
|---|
| hsqldb-2.5.0.jar | 3d1a26905a82ccb66da8f63efa443b5b |
| hsqldb-2.6.1.jar | 855805d373e8ea58e75913ded352338a |
| hsqldb-2.7.0.jar | 7a2c69826a293cb7bd67023360f62ecb |
| hsqldb-2.7.1.jar | 0d99b8af583b80eb114d9d483300bee5 |
MonetDB
| driver | checksum |
|---|
| monetdb.jar | 03ec16f702d64a55b108efdc482ee305 |
| monetdb.jar | dac7e5b87e62dd843a60d48a7397dc08 |
MongoDB
| driver | checksum |
|---|
| mongo-java-driver-3.12.14.jar | 1b5d0f0594fd19a1dc6f83c6f246be35 |
MSSQL
| driver | checksum |
|---|
| mssql-jdbc-11.2.1.jre11.jar | 7e5ab3ba6926ade25378cf871e2ae6a8 |
| mssql-jdbc-11.2.3.jre11.jar | a3979da723792811c5bb8db86102d557 |
| mssql-jdbc-11.2.3.jre11.jar | 35acf0eb21d67f6e993de82c9922f5a5 |
| mssql-jdbc-12.1.0.jre11-preview.jar | 7b8e148aa21b10f0f403aff24e82bf96 |
| mssql-jdbc-12.1.0.jre11-preview.jar | e95a57ed0edbca6644b6b5869a78c6ba |
| mssql-jdbc-12.2.0.jre11.jar | dd6efff9a4af32a2114f7c442a917aac |
| mssql-jdbc-12.2.0.0.jar | 823b86fbaf6308b2e165418a27ae60ef |
MYSQL / MariaDB
| driver | checksum |
|---|
| mariadb-java-client-3.0.7.jar | 505a77fb9ed11de08a84cd83c090f1dd |
| mysql-connector-java-8.0.30.jar | 923639aff48f9a47fa6c7c9025859f5c |
| mysql-connector-java-8.0.31.jar | da96f0f83ff811921c044b8ea407f254 |
| mysql-connector-java-8.0.32.jar | 3ba9d1a80e33ec5c5d55d752e0a76677 |
Oracle
| driver | checksum |
|---|
| ojdbc10-19.16.0.0.jar | 6a1563bd36d3590e55c354f0e73f5025 |
| ojdbc11-21.7.0.0.jar | e2809f4d4a43cf59ff7fa1137a25d5e6 |
| ojdbc11-21.8.0.0.jar | 4a5bd2c2ed6843ad2c34d22c2b46d9d2 |
| ojdbc11-21.9.0.0.jar | 6aaaf331683c4972ada2ce65a03f4380 |
PostgreSQL
| driver | checksum |
|---|
| postgresql-42.3.3.jar | d4b8c2d0a3bc36aefb6a165c23498697 |
| postgresql-42.5.1.jar | c760d13432898f1225463ac4f85587fb |
| postgresql-42.5.2.jar | 33968b135f52c8a5aaf7cbf07f77ce16 |
| postgresql-42.5.3.jar | 38ae934c5e1e7855081491285fbb4f9f |
Redshift
| driver | checksum |
|---|
| redshift-jdbc42-2.1.0.12.jar | 5642139d76a38c5947d13e9ffe91685d |
| redshift-jdbc42-2.1.0.13.jar | 25a732f609c86dccdd19dc2973154b8c |
| redshift-jdbc42-2.1.0.14.jar | 8543fa6179d21891e7bb568775315a61 |
Snowflake
| driver | checksum |
|---|
| snowflake-jdbc-3.13.27.jar | c6c15cc4bc870f66ee2fbd99e7c7ddb1 |
| snowflake-jdbc-3.13.28.jar | c83ad0878927f76e555d38f4a08bb5a2 |
| snowflake-jdbc-3.13.29.jar | 5ec06629ac3859bf2d5e157da48e01d5 |
| snowflake-jdbc-3.20.01.jar | a91e776687ecede6635a655a79ec9cf1 |
SAP Sybase
| driver | checksum |
|---|
| jtds.jar | 1b8f4ecce357e0679ecaa102560eb0ca |
| jtds-1.2.8.jar | 793d8021b715bdf05fdbc6d46fb8e914 |
| jtds-1.3.0.jar | a0e43823e84f297f113ec60e33b1feba |
| jtds-1.3.1.jar | 079f16ab8ba61a17dfdee426d4392d88 |
Create a connection
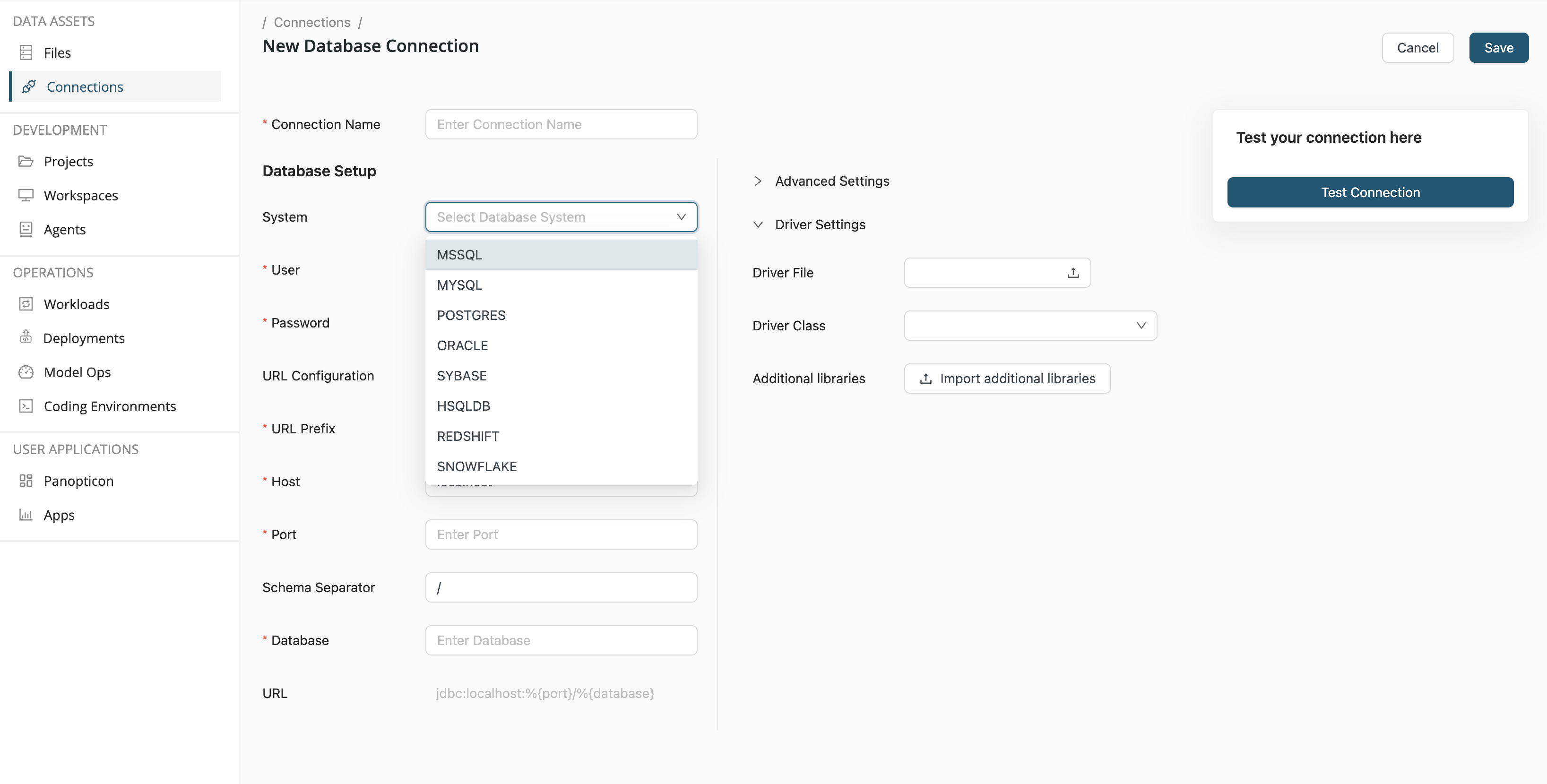
To create a database connection, the following information is required:
- Connection name - The name you give to the connection
- System - The choice of database, given in the dropdown list
- User - The user of the database
- Password - The user's password
- URL Prefix - The URL of the database
- Host -
- Port - The port on which the database is available, e.g. 5432 for PostgreSQL
- Database -
Provide additional files for secure authentication
Typically, you might connect to a database using a username and password. While convenient, this method can be vulnerable to cybersecurity attacks. You can configure hardened authentication using certificates (like .crt, .pem, .jks, or .p12 files).
To configure cert-based authentication, follow these steps:
-
On the Database Connection configuration screen, open the Driver Settings section.
-
Click the Import additional libraries button and browse for the certificates you need for the authentication.
-
Reference the files in your configuration with the %{_internal_files/<filename with extension>} macro.
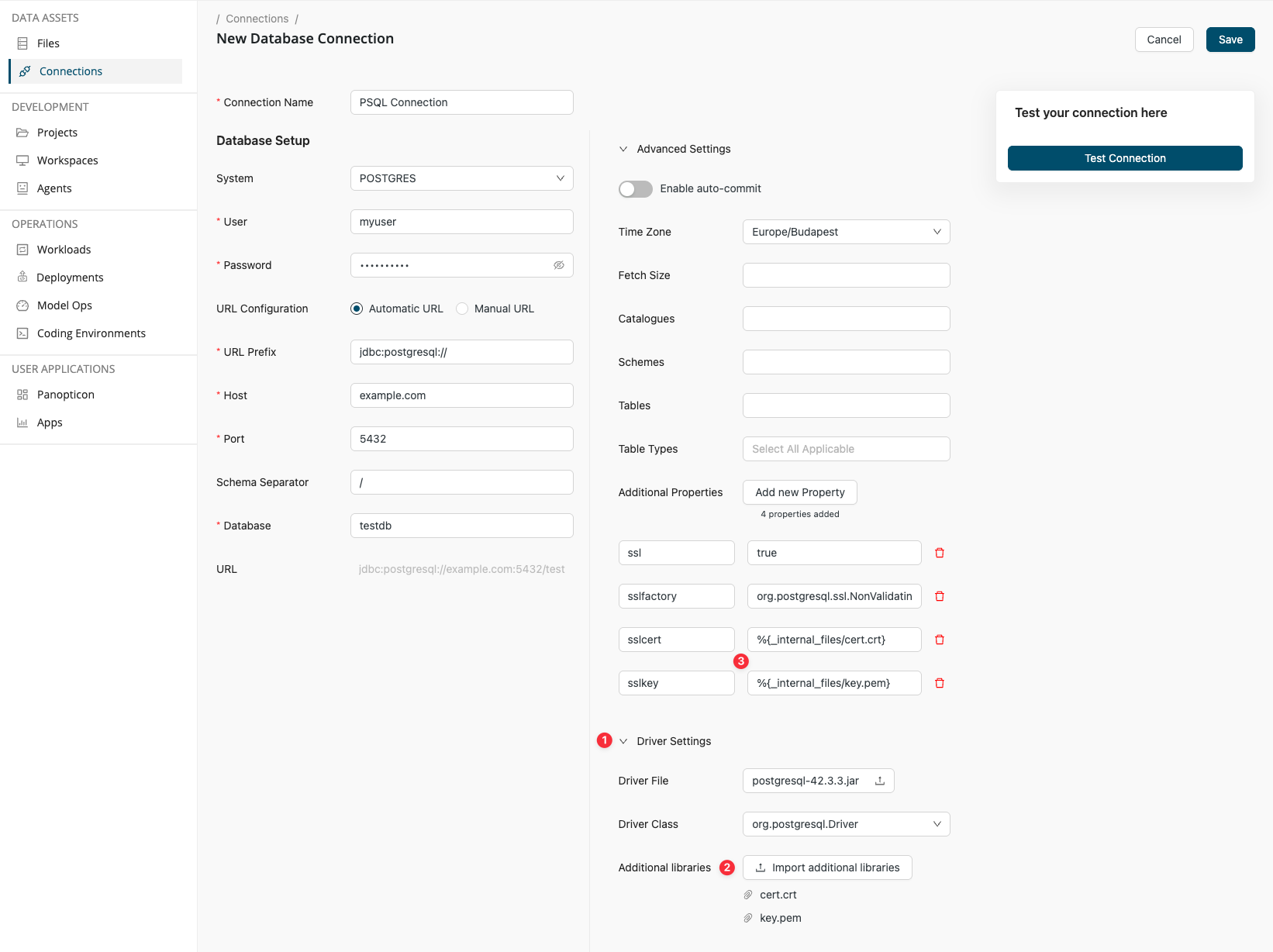
The same works for Manual JDBC URL configuration too. In that case, the JDBC connection string for the above connection takes the following form:
jdbc:postgresql://example.com:5432/testdb;ssl=1;sslfactory=org.postgresql.ssl.NonValidatingFactory;sslcert=%{_internal_files/cert.crt};sslkey=%{_internal_files/key.pem}

